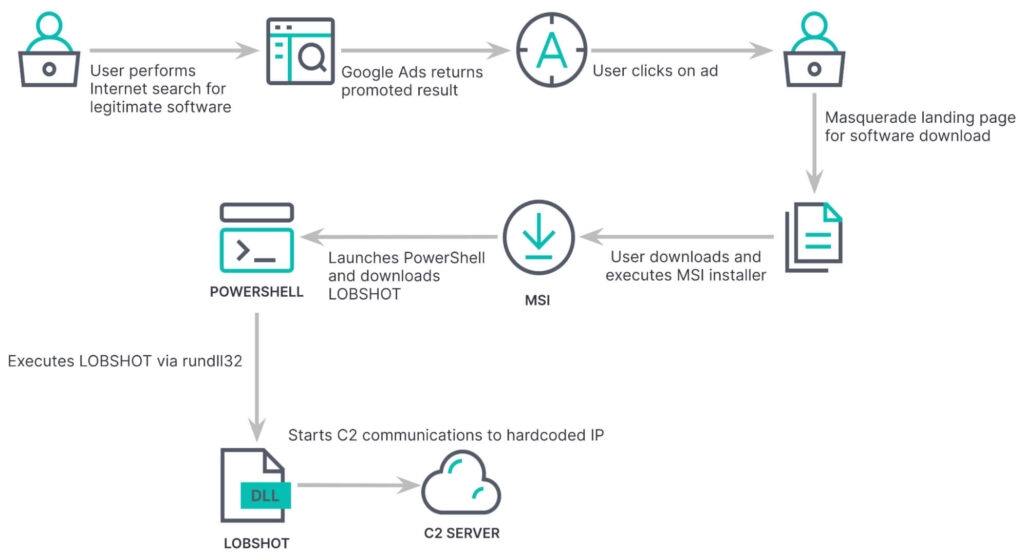
Security researchers discovered a new malware known as LOBSHOT, which is being distributed using Google Ads that allow threat actors to cautiously take over the infected Windows device via using hVNC. Well, hVNC is Hidden Virtual Network computing is a calculated means for the malware to control the machine without the victim’s knowledge. The Google Ads campaign impersonated numerous websites such as Trading View, VLC, ZIP, OBC, Notepad++, CCleaner, Rufus & more apps. Although these websites pushed malware instead of distributing the actual applications, the malware that was distributed includes RedLine Cobalt Strike, Gozi, Royal Ransomware, SectoRAT, and Vidar. A report from the security firm Elastic Security Labs mentions that LOBSHOT malware was being spread through Google ads, and these ads campaigns promoted authentic AnyDesk remote management software, but then it led to the fake Anydisk website at https://www.amydecke[.]website. The website pushes a malicious MSI file that executed a Powershell command to download a DLL from download -cdn[., a com], a domain actually associated with TA505/Clop ransomware group. Read: Evil Extractor, Data Theft Tool Causing Havoc in US & Europe Although, as per, the threat researcher of Proofpoint, Tommy Majdar, told Bleeping Computer that the domain has its ownership changed in the past, so it is not known now if the TA505 is still using it or not. Now the Download DLL file is actually LOBSHOT malware, and it will be saved in the C:/ProgramData folder & then it is executed by RunDLL.32.exe. Elastic Security Labs mentions, “We have observed over 500 LOBSHOT malware samples since last July. The samples we have observed have complied as 32-bit DLLs or 32-bit executables typically ranging around 93 KB to 124 KB”. Once the malware is executed, it checks if the security software, i.e., Microsoft Defender, is running and, if detected, ends the execution to stop being detected. However, if the defender is not detected, then the malware will configure Registry entries to start automatically when it logs into Windows and transfer system information from the infected device, which includes running processes. After that, the malware also checks for nine Microsoft Edge wallet extensions, Thirty-two Chrome cryptocurrency wallets, and eleven Firefox wallet extensions. Now after listing the extensions, the malware then executes a file in C:/Program Data. Although, the file isn’t there in their analysis, so the security firm isn’t sure whether the file is used for stealing data or any other motive. However, stealing cryptocurrency extensions is pretty common; the security firm Elastic Labs discovered that the LOBSHOT malware included hVNC modules which then allow the threat actors to access the infected machine silently. As per the Elastic Security Labs, the malware launches an hVNC module that allows the threat actors to control the hidden desktop using the machine’s mouse & keyboard as if the machine was in front of them. Well, at this point, the victim’s device starts sending screen recordings, which represent the hidden desktop to a listening client that is being controlled by the threat actors, says the security firm. Furthermore, the threat actor then communicates with the client by controlling the keyboard, moving the mouse, and clicking buttons. These abilities let the attacker take full control of the infected device Moreover, by utilizing the hVNC, the attacker now has full control over the machine, allowing them to execute commands, steal data and deploy malware further. As we know, AnyDesk or similar remote access software is commonly used, and the malware is probably used to get initial access to the corporate networks and then spread to other machines. Read: Phishing Scams Targeting US Taxpayers with Remote Access Malware